NuMicro® M2354 Series Is Capable of Mitigation to Power Analysis Attacks for Cryptographic Hardware Accelerators
Information security relies not only on cryptography algorithms but also on the protection of the machine itself. However, when system chips are usually running, they inadvertently leak some messages on physical features. These messages will be spread outside the system chip through physical phenomena such as voltages, currents, and electromagnetic waves, and attackers can analyze these exposed messages to reverse analyze the keys in the chip. This type of attack that uses the physical information leaked from the operation of password systems to crack the system is called a side-channel attack.
M2354 is developed by Nuvoton used to meet the needs of the times for MCU performance and security; it provides accelerators for the cryptography algorithm of various hardware, and multiple message protection functions including AES, ECC, RSA, HMAC, and high-quality True Random Number Generators (TRNG). It is also equipped with an exclusive Key Store to save keys, allowing it to be applied in applications with high-security requirements. Not only does it have extremely high performance, it can also block intrusions by attackers and stealing of messages effectively, whether the attack originated from the network or from attacks to the MCU itself.
M2354 also added side-channel attack protection for the commonly used cryptography algorithms AES, ECC, and RSA to prevent attackers from reverse analyzing the key used using the physical information leaked from MCU operations. The side-channel attack protection for AES can reduce the amount of information leaked from the power and ground terminals during the operation of AES significantly to prevent related information from being captured to analyze its key.
In addition to AES, M2354 also provides the asymmetric encryption algorithm ECC and added side-channel attack protection to increase the information attackers analyze from the power and ground terminals and increase the difficulty of reverse analyzing the key.
M2354 also added the RSA hardware accelerator with side-channel attack protection built-in, preventing the key information from being leaked through the power or ground terminals during operation.
Take RSA for example, if side-channel attack protection was not added, the key used for decoding and its current waveform during decoding will be highly relevant, as shown in the figure below:
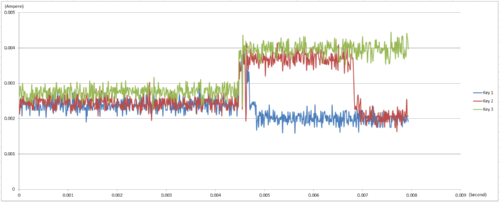
It can be seen from the figure above that the three different RSA keys have significantly different current waveforms during decoding; this shows that information related to the keys is indeed obviously hidden in the current waveform of RSA operation. This allows attackers to easily analyze the current during RSA operation to reverse analyze the key used.
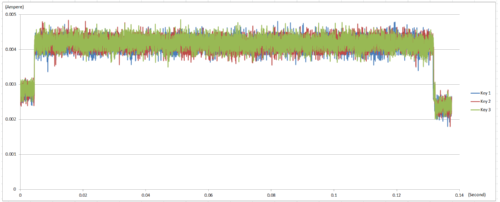
Therefore, effective side-channel attack protection must be able to be hidden in RSA operations. As for the key messages leaked from the current, it can be seen in the figure below that after the RSA side-channel attack protection function is enabled in M2354, the difference between the different keys could not be distinguished as obviously from the current information while RSA is operating. This shows that after the side-channel attack protection function is enabled, it can effectively suppress key information being leaked from the operating current.
Besides relying on the strength of cryptography algorithms, whether the system itself can effectively protect related keys from being stolen is also extremely important when it comes to information security. A side-channel attack is a very common attack method for stealing system keys; therefore, the protection for complete information security is also a very important link. The AES, RSA, and ECC cryptography algorithms of M2354 not only provide hardware accelerators and high-performance data encryption, protection for side-channel attacks is also provided for each one of them. It protects the security of data transmission through networks and also protects against attacks to the MCU itself, truly achieving complete information security.