An Introduction to TF-M Open Source Project for MCU Security
M2354 is a microcontroller manufactured by Nuvoton; its rich security designs make this microcontroller particularly suitable for applying in the security field, especially for IoT devices connected through the internet.
Since IoT devices are exposed to the internet, they require sufficient security mechanisms to protect the privacy of users and prevent hacker attacks and intrusions from turning them into tools for hacking. In order the protect the security of networked devices, M2354 not only adopted the Arm V8-M Trust Zone architecture for its security design, it also uses the open-source firmware (TF-M) from Arm, forming complete security architectures for IoT application platforms together.
The M2354 security platform is structured on an unmodifiable security component; it includes a bootloader, device life cycle management, cryptography hardware accelerator, Key Store, and Trust Zone technologies. It is used with a second bootloader process (BL2) that passed Root of Trust verification and is updatable, as well as the Trusted-Firmware-M to ensure the security of itself and to further provide various security services. Among these features, the TrustZone technology is also used to isolate the operations of the security services of the users’ application processes and operating systems, further ensuring the security of the system's operation.
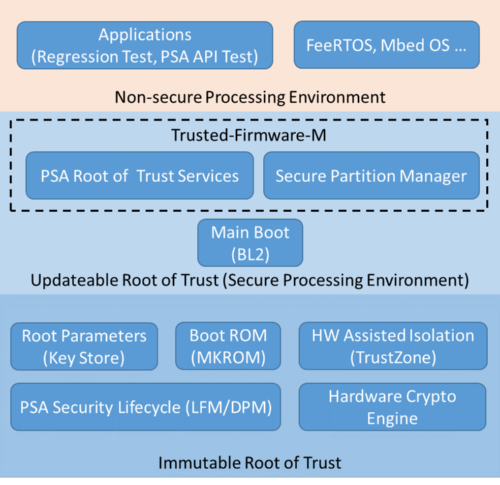
▲The security architecture of the M2354 platform
Under this security architecture, all communications and transmissions between IoT devices and the cloud will have encryption and decryption services and the storing of sensitive data provided under the prerequisite of hardware isolation.
The figure below is an example of the operation of an IoT device under the security architecture; this device uploads the temperature of the location of the device to the cloud.
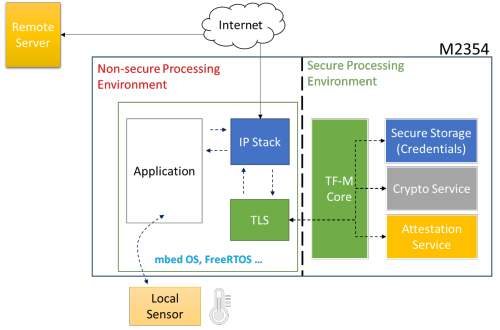
First of all, after the device is activated, a registration mechanism is used first to pass the authentication of the cloud service and prove the legality of this device. This authentication mechanism will be completed by services in the secure zone of TF-M to ensure security and privacy during the entire registration authentication process.
After the registration authentication of the device is completed, the data measured by the device can now be uploaded to the cloud. This part uses the TLS (Transport Layer Security) transmission protocol to ensure that the connections with the cloud are encrypted and protected, in which its encryption and decryption processes can be completed by the encryption and decryption services in the isolated area of TF-M to ensure that the keys and other secret information used during encryption and decryption will not be exposed to non-secure zones.
Application processes developed by the user are used in non-secure zones to realize all functions of the product.
Under the M2354 security platform architecture, since product developments are concentrated in non-secure zones, and all required security functions are realized by TF-M and isolated in the secure zone, this allows users to focus more on developing product functions and not have to worry about security issues, reducing the development schedule and difficulty significantly while maintaining the necessary security to meet the security requirements of IoT devices.
In addition to the various software and hardware security designs mentioned above, in order to allow M2354 IoT devices to obtain the best protection results, M2354 further introduced protection mechanisms against fault injection and side-channel attacks to protect IoT devices from being attacked by hackers using a physical injection of system errors, or monitoring of voltages, currents or electromagnetic waves while the device is operating. This will allow IoT devices based on the M2354 security platform to not only have protection ability against attacks from networks but also have resistance from physical attacks, upgrading the security of the device to a higher level.
For users who are interested in the M2354 security platform, the NuMaker-M2354 evaluation board can be purchased from Nuvoton’s online store (http://direct.nuvoton.com), and the latest TF-M firmware can be downloaded directly from GitHub (https://www.trustedfirmware.org/projects/tf-m/).
M2354 has rich and complete online resources on the official website of Nuvoton, suitable for new users to learn from and get familiar with the operations of the Arm TF-M security platform, providing the most solid support for the development of secure IoT devices.